Within the realm of IT service management, ITIL serves as a globally recognized framework providing guidelines and best practices for aligning IT services with the needs of businesses. A critical element in meeting and maintaining compliance with ITIL standards involves the implementation of CIS Hardening. Understanding ITIL and its Emphasis on Service Excellence: ITIL represents […]
In the bustling city of federal data, where sensitive government information flows like a crucial trade route, security isn’t just a priority, it’s a sworn oath. And for any government agency handling classified information, adhering to the Federal Information Security Management Act (FISMA) isn’t a suggestion, it’s a legal mandate. Within this robust framework, stands […]
In the realm of IT governance and management, COBIT (Control Objectives for Information and Related Technologies) stands as a leading framework providing guidelines and best practices for aligning IT activities with business goals. An essential aspect of achieving and maintaining compliance with COBIT involves the implementation of CIS Hardening. Understanding COBIT and its Emphasis on […]
In the realm of government cloud security, the Federal Risk and Authorization Management Program (FedRAMP) sets the benchmark for stringent security standards. FedRAMP compliance is mandatory for cloud service providers seeking to serve government agencies. One pivotal element within the landscape of achieving and maintaining FedRAMP compliance is the implementation of CIS (Centre for Internet […]
In the bustling realm of e-commerce, where data dances from point-of-sale to payment processors, security should be the tango you master first. For businesses handling sensitive payment card information, complying with the Payment Card Industry Data Security Standard (PCI DSS) isn’t a suggestion, it’s a vital step to avoid costly fines and reputational damage. And […]
In today’s rapidly evolving cyber threat landscape, organizations face increasing challenges when it comes to protecting their sensitive data and securing their infrastructure. To address these challenges, frameworks like the NIST Cybersecurity Framework (CSF) provide a comprehensive set of guidelines and best practices. However, one crucial piece of the puzzle that is often overlooked is […]
The ISO/IEC 27001 standard serves as a cornerstone in establishing and maintaining Information Security Management Systems (ISMS). Within this framework, implementing CIS (Centre for Internet Security) Hardening emerges as a fundamental and mandatory step in fortifying an organization’s security posture. Let’s delve into why CIS Hardening is integral to achieving ISO/IEC 27001 compliance: Adhering to […]
In today’s digital landscape, the protection of personal data stands as a paramount concern. The General Data Protection Regulation (GDPR) imposes stringent requirements on organizations handling the personal data of European Union residents. Complying with GDPR necessitates robust security measures, and CIS (Centre for Internet Security) Hardening plays a pivotal role in meeting these mandates. […]
In the landscape of cybersecurity and data protection, achieving compliance with regulatory standards is paramount. However, while compliance frameworks provide essential guidelines, they often overlook a crucial element: server hardening. This missing piece in the puzzle of continuous compliance plays a pivotal role in fortifying systems against evolving threats, complementing, and strengthening adherence to regulatory […]
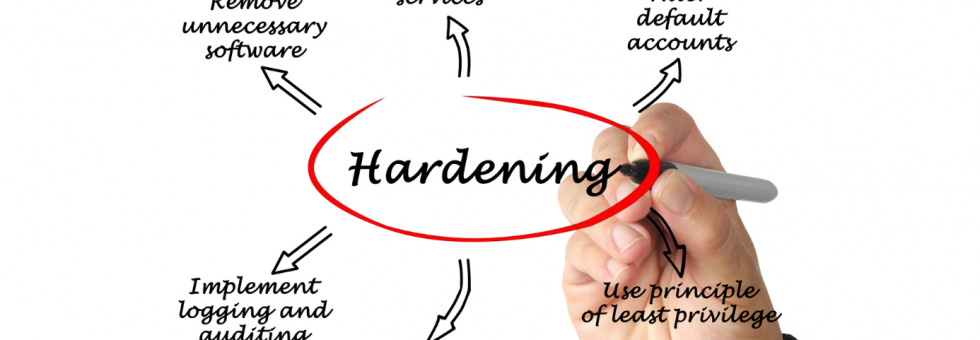
Server Hardening The server hardening process reduces your business’ attack surface and helps you guard against ransomware, malware, and other cyberthreats. You can follow this process to protect all points of entry against cyberattacks, address cybersecurity weaknesses, and optimize your security posture. What Is Server Hardening? A server is a computer program or device that […]